A new variant of the Glupteba malware dropper is using the Bitcoin blockchain to fetch command and control (C2) server domains from Bitcoin transactions marked with OP_RETURN script opcodes.
Glupteba has been previously distributed as a secondary payload by the Alureon Trojan as part of a 2011 campaign designed to push clickjacking contextual advertising, as well as by the threat actors behind Operation Windigo onto their targets’ Windows computers with the help of exploit kits in 2014, as discovered by ESET’s security research team.
Four years later, in 2018, the malware dropper was again spotted by ESET while being disseminated by a malicious campaign via a Pay-Per-Install scheme, adding all the infected machines to an attacker-controlled botnet.
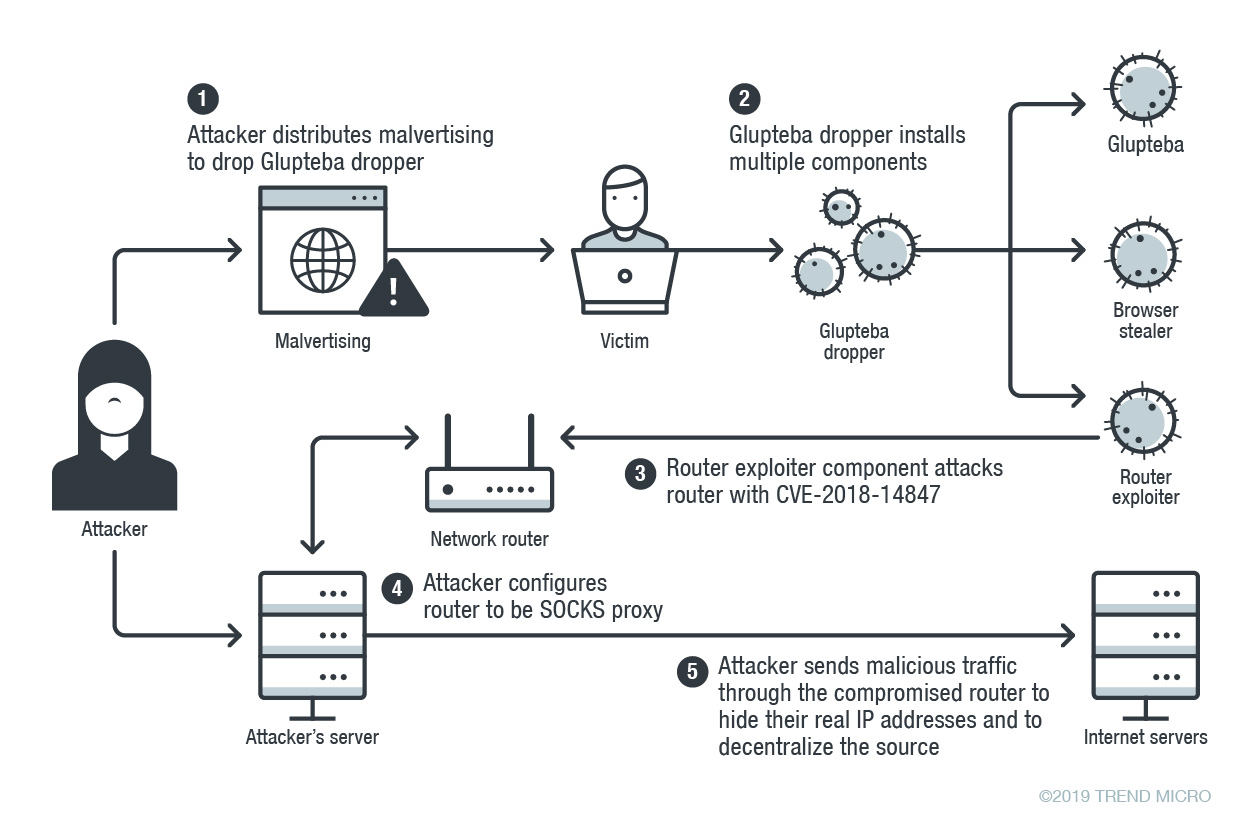
The new version discovered by Trend Micro recently has switched to malvertising as the means of distribution and it comes with two more modules besides the newly added Bitcoin blockchain C2 updater, namely an info stealer and an exploit that targets local MikroTik routers.
Retrieving C2 server info from Bitcoin transactions
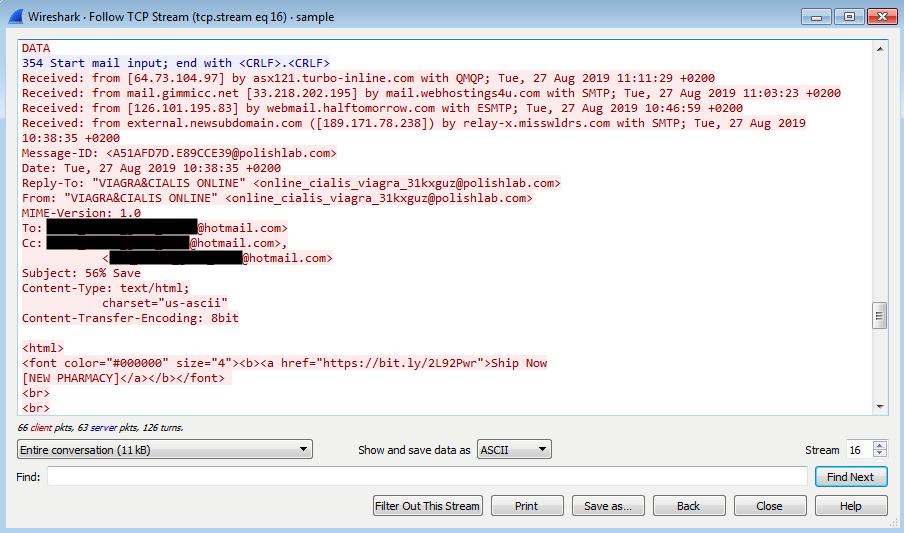
The new variant uses Bitcoin transactions info parsed from a hardcoded Bitcoin address to retrieve C2 server addresses using a discoverDomain function designed to work on a schedule or when triggered by the attackers.
This function works by enumerating Electrum Bitcoin wallet servers using a list available on GitHub, subsequently querying “the blockchain script hash history of the script with a hardcoded hash.”
After retrieving all related Bitcoin transactions, it parses all of them while looking for the OP_RETURN instruction that marks the AES encrypted data containing the malware’s C2 server domains.
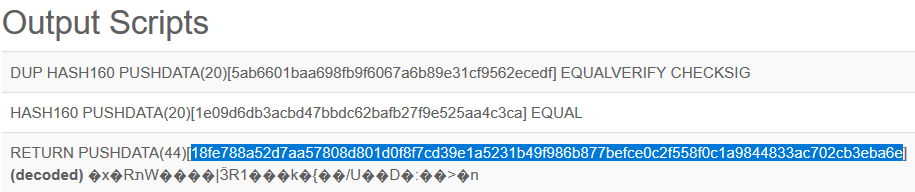
“This technique makes it more convenient for the threat actor to replace C&C servers,” found Trend Micro’s researchers while analyzing the new Glupteba variant.
“If they lose control of a C&C server for any reason, they simply need to add a new Bitcoin script and the infected machines obtain a new C&C server by decrypting the script data and reconnecting.
Exploits routers, steals info, proxies malicious traffic
Once it infects a computer, the dropper will start collecting system info which it stores within the Windows registry, data that will later be encrypted with an AES cipher and uploaded to the malware’s C2 server with a POST request.
The malware will also use several methods to elevate its privileges to run with SYSTEM permissions, as well as functions designed to check for anti-malware solutions, to add scanning exclusions and firewall rules, and to reach out to the C2 server to check for any new commands.
Glupteba also has backdoor functionality which allows the attackers to transform the infected machine into an XMR mining bot, to download and execute files, to take screenshots, and more.
The info stealer component added to this new variant makes it possible to collect browser profiles, cookies, and accounts names, and to extract saved passwords from the Google Chrome, Opera, and Yandex web browsers, with all the data being exfiltrated to an information collection server.
Glupteba’s router exploiter searches or and attacks all the MikroTik routers it finds on the victims’ local network with the help of an exploit designed to target the CVE-2018-14847 vulnerability. Upon successful exploitation, the router’s admin credentials are harvested and sent to the malware’s C2 server.
“A compromised router will be configured as a SOCKS proxy to relay malicious traffic, matching the original purpose of the Glupteba botnet on Windows,” found the researchers.
A comprehensive list of indicators of compromise (IOCs) including malware sample hashes, IP addresses, and domains is available as an appendix [PDF] to Trend Micro’s analysis of this new malvertising campaign distributing the Glupteba dropper.

Be the first to comment